Source code review with AutoBugle
Note: Auto Bugle is a discontinued project
This article is kept just for reference. I will try to package the source code and give it as a download at some point.
Some time ago I start creating a list of google queries (Bugle) people could use to hunt bugs in source code available in the web. The project started before Google Code Search, so the only way to point to source code was using the Filetype and ? * . operators which worked pretty well. After a couple of months Google announced the Code Search service and the accompanied API which made things much more interesting. Using the new Google service people can supply full regular expression when searching and pinpoint to Bugs a bit more accurately.
Anyway, to cut a long story short, utilising jQuery, Google Code Search API and Bugle, I created an automated version of the Bugle project which looks as close as possible to a desktop based source code review tool.
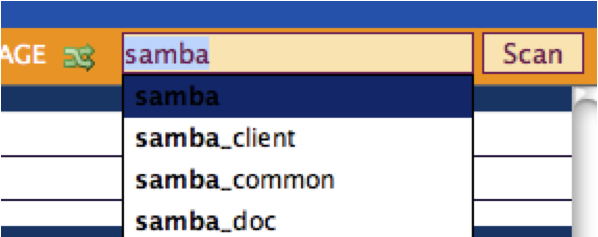
To demonstrate Bugle Automated I will be looking for bugs in Samba. The first step is to add the package you want to inspect in the Scan field, as you can see below there is Auto Complete functionality available suggesting possible packages while you type a name.
After choosing a package, press scan an Bugle will do the rest.
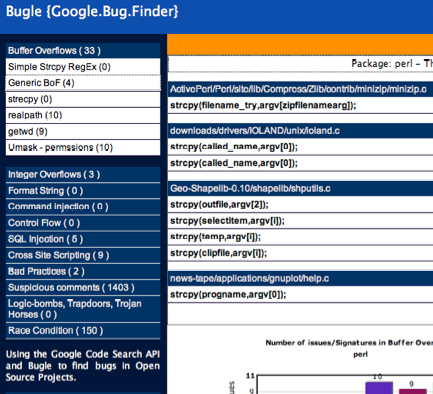
The first screen you see is a bit empty , both the Main Panel and the Stats Panel will load as soon as you choose a vulnerability category from the left side. Bugle displays the number of issues of each category, so you can immediately get an general idea on where you might find a bug.
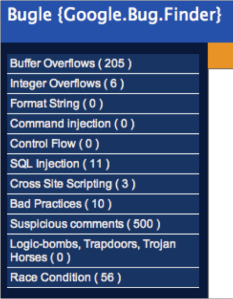
As soon as you choose a category a sub menu will be revealed, presenting all the different signatures in that category. At the same time the statistics Panel will load and all the relevant graphs for the project/categories and categories/signatures will be displayed.
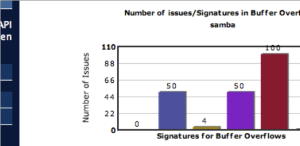
Next we choose the Buffer Overflows category, with 205 hits and then the Generic BoF signature (with 50 hits). The Main Panel loads and then we can see each individual line with a possible bug. We scroll down until we find something that could be a vulnerability and click on that line.
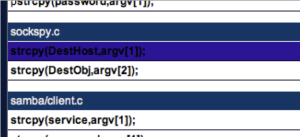
We click the Line 117 of samba-1.9.15p8.mvs/source/sockspy.c and we inspect the code in the Code Snippet dialog. Then we scroll down until we find the line with the yellow highlighted text
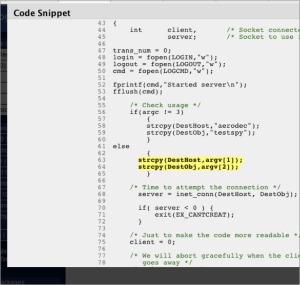
We can see that strcpy(DestHost,argv[1]); is copying the arv[1] into the DestHost buffer which has 256 chars size. Now we can guess that if we pass in the command line DestHost larger than 256 chars we can create a buffer overflow condition. (Note that this bug in sockspy.c is in a very very very old version of Samba)
That's Bugle Auto Scanner, hopefully this will assist in discovering and fixing bugs out there.